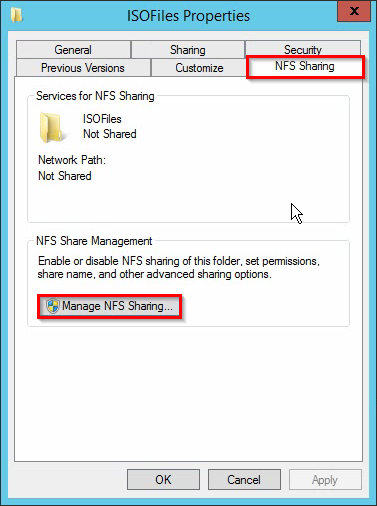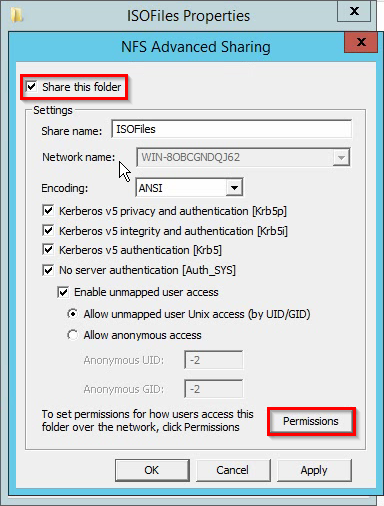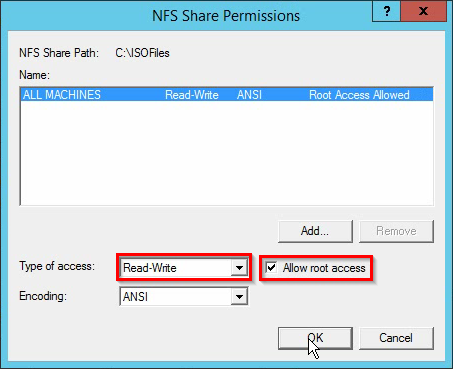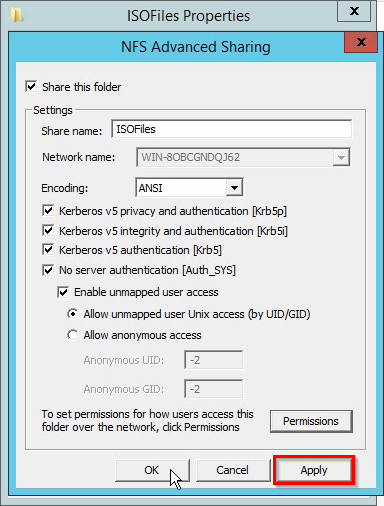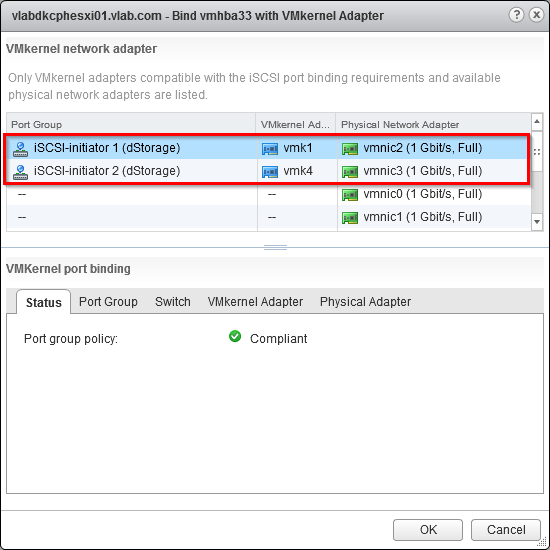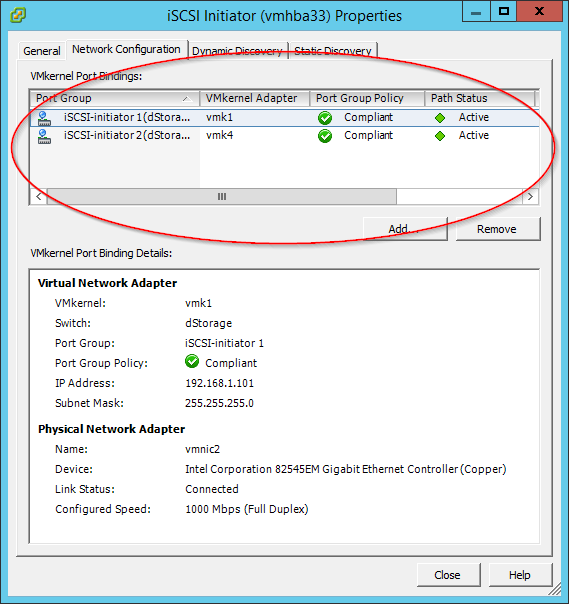

How to set a password on console ports
The console port is considered the primary terminal line and should be protected by a password.
Switch(config)#line console 0
Switch(config-line)#password console
Switch(config-line)#login
Executing the login command makes sure the console port will prompt you for authentication. You cannot use the login command without setting a password first or that line simply won’t be usable.
You can set a password on all console ports starting from line 0 – 16. Upon setting this password a prompt will appear at first connection.
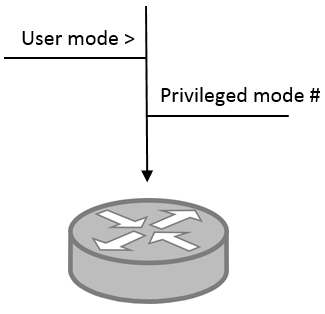
How to set a password on privileged mode
Switch(config)#Enable secret edCkdso!kdl
How to prevent console messages from disrupting your inputs
Switch(config)#line console 0
Switch(config-line)#logging synchronous
How to change or disable the console’s default timeout value from 10mins
Switch(config)#line console
Switch(config-line)#exec-timeout 0 0
The exec-timeout value is determined in seconds.
How to set a Telnet password
Telnet is referred to as the vty line in Cisco IOS.
First you have to see how many lines you have available. Routers usually have considerably more than switches, and then set the password for all lines possible.
Switch(config)#line vty 0 ?
<1-15> Last Line number
<cr>
Switch(config)#line vty 0 15
Switch(config-line)#password telnet
Switch(config-line)#login
Remember to always set the Telnet password in a production environment, but use a unique one as Telnet is not an encrypted line!
How to set a password on the auxiliary port of a router
First check how many lines you have and then set the password. For this I’ll showcase the login command functionality.
Router(config)#line aux ?
<0-0> First Line number
Router(config)#line aux 0
Router(config-line)#login
% Login disabled on line 0, until ‘password’ is set
Router(config-line)#password aux
Router(config-line)#login
How to set up Secure Shell (SSH)
A hostname and a domain name are needed for the encryption keys to be generated.
Switch(config)#hostname vlabdkcphsw001
vlabdkcphsw001(config)#ip domain-name itvlab.com
vlabdkcphsw001(config)#username mkbn password ssh
The name for the keys will be: vlabdkcphsw001.itvlab.com
Choose the size of the key modulus in the range of 360 to 2048 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable…[OK]
Vlabdkcphsw001(config)#
*mar 1 1:22:45.821: %SSH-5-ENABLED: SSH 1.99 has been enabled
Enable SSH version 2
vlabdkcphsw001(config)#ip ssh version 2
Configure the desired access protocols allowed on the vty line
vlabdkcphsw001(config)#line vty 0 15
vlabdkcphsw001(config-line)#transport input ?
all All protocols (NOT RECOMMENDED!)
none No protocols
ssh TCP/IP SSH protocol
telnet TCP/IP Telnet protocol
To allow SSH and Telnet at the same time type the following
vlabdkcphsw001(config-line)#transport input ssh telnet
How to encrypt the passwords from sh running-config
Every password but the secret password are visible from the sh running-config command by default. The way the encryption of the passwords work in the Cisco IOS is a little weird I think. You can use the service password-encryption to encrypt the passwords and then turn it off and they will still be encrypted.
vlabdkcphsw001(config)#service password-encryption
You can leave the service encryption ON, but this would take up processes. Use the show running-config command to first show that they have been encrypted.
vlabdkcphsw001#sh running-config
After you have verified the password encryption then you can turn off the encryption service.
vlabdkcphsw001(config)#no service password-encryption
If you execute the service encryption before setting the passwords then you don’t have to use the show running-config command. So in summary you cannot use the commands service password-encryption and no service password-encryption consecutively without the show running-config in between or your passwords won’t be encrypted!
How to turn off DNS
If you enter an IP address in privileged mode the switch or router will automatically assume you want to telnet by default. And if you type a name it will automatically try to resolve it through DNS.
So have you ever seen this?
Switch#mikkel
Translating “mikkel”…domain server (255.255.255.255)
% Unknown command or computer name, or unable to find computer address
This is because DNS is turned on by default, and you are forced to wait the timeout. To turn it off use the following command:
Switch(config)#no ip domain-lookup