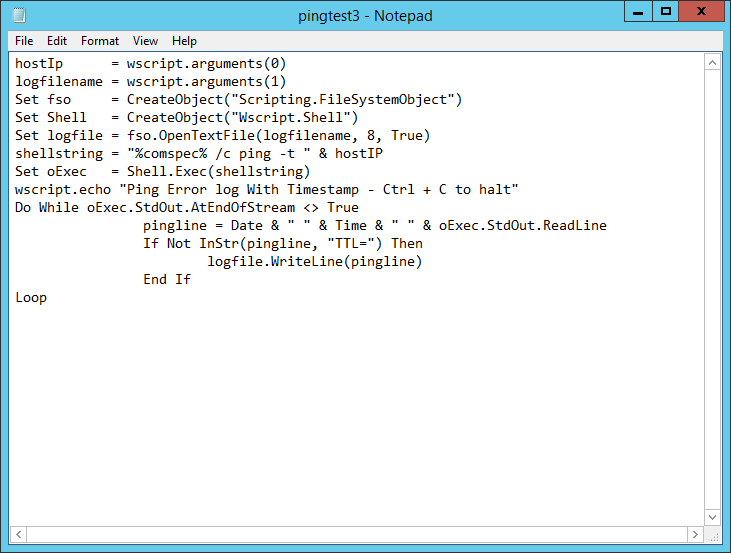
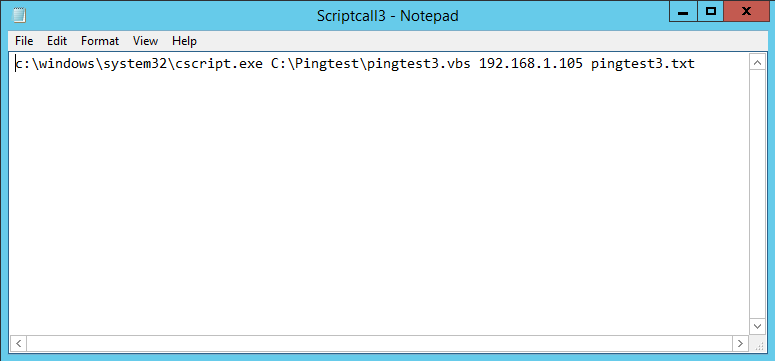
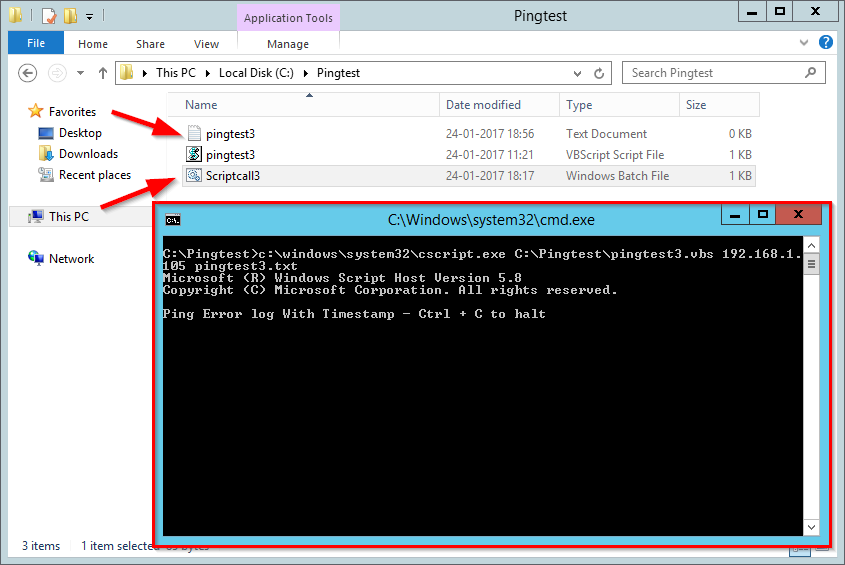
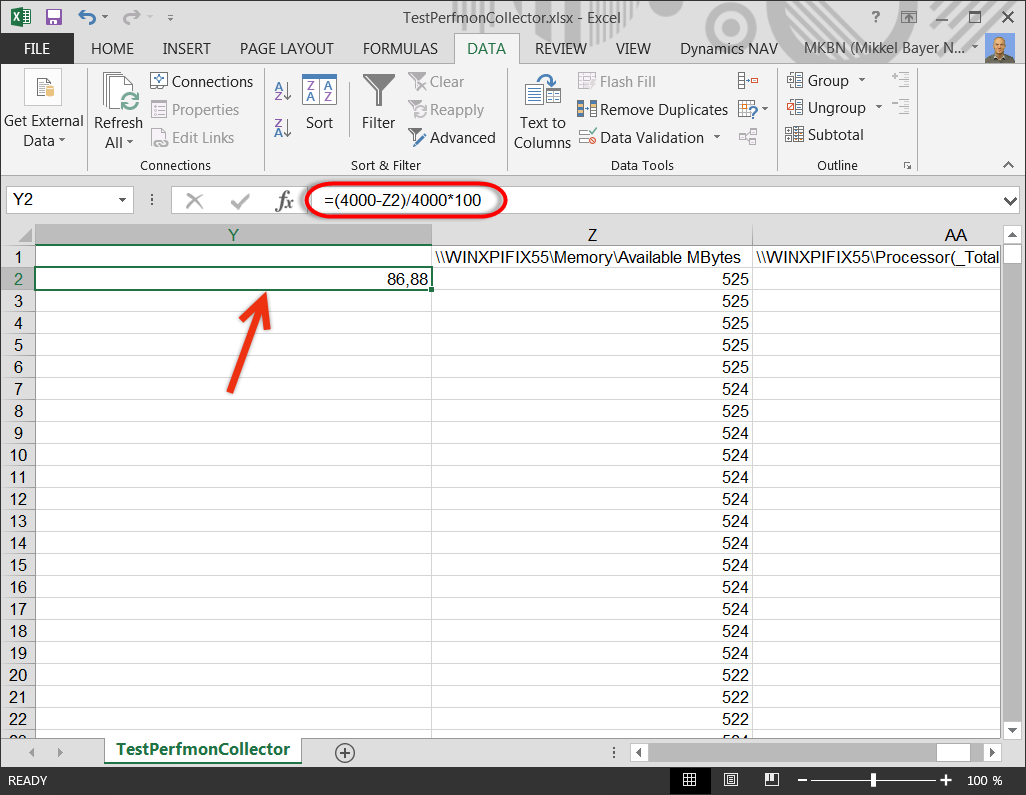
Ooooh dear Microsoft.. We’re in 2022 and still I have to run Powershell commands on a M365 ressource for something I kinda see as standard. Or rather I think this should and could be handled much smarter.
Say you have a ressource named “Meeting room” used for booking a physical room somewhere down the hallway.
Recurring meeting that conflict with just a single meeting will reject the recurring meeting entirely. To avoid this you might be tempted to enable
Set-CalendarProcessing “Meeting toom” -AllowConflicts $true
But that will allow double bookings and isn’t the greatest.
Firstly, some tenants may not receive e-mail confirmations when a ressource is booked, so run this:
Set-CalendarProcessing “Mødelokale” -ProcessExternalMeetingMessages $True
Next, to modify the behaviour of the ressource to allow a recurring meeting that still conflicts, run:
Set-CalendarProcessing “Meeting room” -ConflictPercentageAllowed 80
Set-CalendarProcessing “Meeting room” -MaximumConflictInstances 10
Above commands will allow the person who booked to receive confirmation emails for accepted dates, and confirmation emails for dates rejected because there was a conflict. Obviously, the above commands allows 10 maximum conflicts, or up to 80% conflicts, exceeding those parameters and the recurring meeting will be rejected entirely.
More on the subject here but the essence is;
So, for example, say a room mailbox is configured with the following settings:
AutomateProcessing : AutoAccept
AllowConflicts : False
AllowRecurringMeetings : True
ConflictPercentageAllowed : 40
MaximumConflictInstances : 6
- A recurring meeting request which repeats 10 times (10 instances) is sent to the mailbox. Now let’s suppose 5 out of 10 (or half) of the instances for that recurring meeting occur at the same time other meetings are scheduled in the calendar. In this case, the 50% conflict ratio exceeds the ConflictPercentageAllowed setting of 40.
The result: The entire meeting request is rejected and the room sends a message back to the meeting organizer with the subject Declined All. The five conflicting instances are declined, as are the other five instances that didn’t conflict with another meeting. - Another meeting request is sent where there are 100 instances of a recurring meeting and 10 of them conflict with existing bookings. In this case the ConflictPercentageAllowed is not exceeded by the 10% conflict rate. However, we exceed the MaximumConflictInstances setting of 6.
The result: Once again, the entire meeting request is rejected and all 100 instances are declined. - For our last example, a recurring meeting request comes to this room where there are 10 instances and only 2 of them conflict with existing bookings.
The result: Since we don’t exceed either MaximumConflictInstances or ConflictPercentageAllowed, the room mailbox accepts the recurring meeting request series but declines to book the two instances that conflict. The meeting instances that don’t conflict are accepted and booked and the room sends three emails back to the organizer, one with Accepted in the subject stating the recurring meeting request was accepted, and two with Declined in the subject for the two conflicting instances.
So by these examples we see how a recurring meeting request with conflicting instances can be accepted or declined based on the calendar processing settings. However, it’s important to repeat that a recurring meeting request instance that conflicts with another booking is ALWAYS declined.